Permissions– the settings that govern who can make changes to files in which circumstance– is not an easy concept. The confusion starts soon after the experience of seeing a file you created is suddenly not editable by you after you put it on the network share. Today I learned that Linux permissions are assembled from different sources, and understanding how these pieces fit together has helped me create the environment I need. Here are the basic blocks:
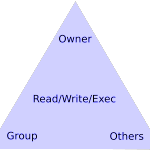
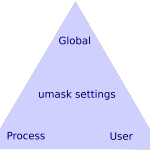
Each of these pieces has an impact on a user’s ability to create, save, and delete files. A common scenario is the owner of a file wants to share it on a network folder, but his colleagues can’t open it! Setting any one of piece is often not enough to cure frustrations, but getting them all assembled correctly creates a very satisfying scheme. The words in the triangles above are arranged on purpose: each triangle represents a group of settings that work together to determine permissions for files and directories.
Read/Write/Execute
-rwxrwxr- 1 root nogroup 1929201 Jan 3 12:11 birthday_party.jpg
- The example file above is owned by root and the group ‘nogroup’. The owner is listed first and the group second. The Linux command to change these is chown. In the case of root, you’ll use sudo and the password. How-to article on the chown command.
- The letters stand for read/write/execute for each type of user. The first dash means that this is a file; a directory would have a D there. The dash at the end means that a permission is not set.
- Types of users are Owner/Group/Others. This means that each file has specific permissions for each type of user, shown in the trio of rwx. The file above allows read/write/execute for the owner, for the group, but it is read-only for Other users. The linux command for this is chmod, and setting the r/w/x permissions is accomplished with a 3-digit number that represents the unique set of permissions. This number is called an Octal. How-to article on chmod and a super easy tool to calculate chmod permissions number.
Umask
Umask is the default setting for any permissions that are not explicitly set using the commands above. This allows a more or less restrictive overall scheme for systems like files servers or web servers. Umask uses the same trio of read/write/execute for each type of user, except that the 3 digit number is calculated differently, and it determines permissions for files AND directories.
Umask is set globally in /etc/login.defs, and it’s set in each user’s profile when /etc/login.defs contains the setting “USERGROUPS_ENAB yes”. Some application processes have their own umask setting, so that will govern permissions on files set by users in the application. Apache and PHP do this to control sessions and prevent unwanted access.; look for umask entries in php.ini and /etc/apache2/envvars.
To view your current umask setting, open a terminal and run the command: umask. The default setting in Linux is 022 where each digit represents the specific permissions for each type of user, shown in the trio of rwx. Sound familiar? The difference is that 0 represents all permissions instead of none. The umask defines the permissions that are NOT available to each user group, so 000 means owner/group/others can all read/write/execute. The linux default of 022 has denied groups and others write/execute to files and write to directories. Conversely, groups and others may read files and directories.
Handy umask Table
| umask Octal Value | Enabled File Permissions | Enabled Directory Permissions |
|---|---|---|
| 0 | rw- | rwx |
| 1 | rw- | rw- |
| 2 | r-- | r-x |
| 3 | r-- | r-- |
| 4 | -w- | -wx |
| 5 | -w- | -w- |
| 6 | --x | --x |
| 7 | --- (none) | --- (none) |